As the world becomes increasingly digital, so do our financial transactions. Smart contracts have become a popular way to secure these transactions, but they are not foolproof. If you want to ensure the safety and security of your smart contract transactions, it’s essential to know how to audit them properly. In this article, we’ll provide a comprehensive guide on how to audit a smart contract, including the tools and techniques needed for a thorough audit.
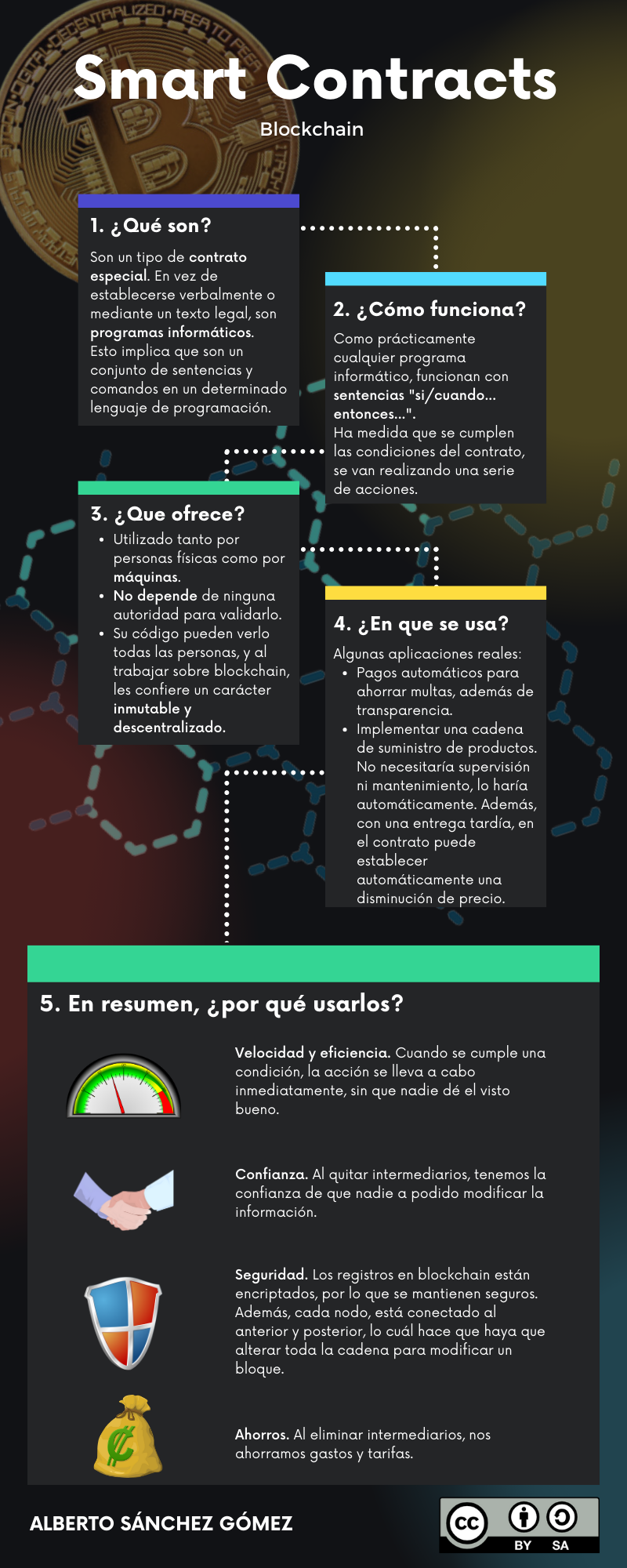
Before we dive into the details of auditing a smart contract, let’s first understand what a smart contract is and why they are becoming more popular. A smart contract is a self-executing contract with the terms of the agreement between buyer and seller being directly written into lines of code. These contracts are stored on a blockchain network, which ensures their security and immutability.
But even with the inherent security benefits of a blockchain, smart contracts are not immune to vulnerabilities. As such, properly auditing a smart contract is essential to ensure that it is free from risks and potential exploits.
Now, without further ado, let’s get started on how to audit a smart contract.
Tools and Techniques for Auditing Smart Contracts
1. Static Analysis
One of the most critical methods of auditing a smart contract is using static analysis tools. These tools examine the code before it is executed, looking at issues such as syntax errors, security flaws, and potential exploits. One popular tool for static analysis is Mythril. This tool is designed specifically for Ethereum smart contracts and can quickly identify vulnerabilities in your code.
2. Dynamic Analysis
Dynamic analysis tools test the smart contract while it is running on the blockchain network, checking for any anomalies or abnormalities. One example of a dynamic analysis tool is Oyente. This tool can detect issues such as gas usage, security vulnerabilities, and potential exploits.
3. Manual Review
While static and dynamic analysis tools are essential for auditing a smart contract, a manual review is also necessary. A manual review allows for a human auditor to examine the code and identify any suspicious or irregular patterns that might not generate alerts from automated tools.
4. Penetration Testing
Penetration testing involves simulating an attack on the smart contract to identify any vulnerabilities or weaknesses in the code. This technique is useful in determining how an attacker might exploit the contract and provides insight into how to mitigate these risks.
Best Practices for Auditing Smart Contracts
1. Use Formal Verification
Formal verification is a mathematical proof of the correctness of the smart contract’s code. While it is a time-consuming process, formal verification provides the highest level of assurance that the contract will function as intended.
2. Follow Solidity Best Practices
Solidity is the programming language used to write smart contracts on the Ethereum network. Following best practices when writing in Solidity ensures that your code is clean, efficient, and secure.
3. Limit the Amount of Ether at Risk
Smart contracts should only hold the minimum amount of ether required to execute the transaction. By limiting the amount of ether held in the contract, you reduce the risk of a catastrophic loss.
4. Use Multiple Auditors
Having multiple auditors review the code provides a more thorough audit and increases the likelihood of identifying potential risks or vulnerabilities.
Conclusion
Auditing a smart contract is an essential process to ensure the security and safety of your transactions. Using a combination of static and dynamic analysis tools, manual reviews, penetration testing, and following best practices will minimize the risks and ensure your smart contract functions as intended. With this comprehensive guide, you now have the knowledge and tools needed to audit your smart contract thoroughly.
Remember to always follow best practices and stay up-to-date with new techniques and technologies to ensure your security measures are always strong.