Cybersecurity and Etical Hackig Blog
-

How to Create an Effective Cyber Security Analysis Report
Are you looking for a comprehensive guide on how to create an effective cyber security analysis report? Look no further! In this article, we will cover everything you need to know about cyber security analysis reports, from the basics to the best practices. Cyber Security Analysis Report: Understanding the Basics A cyber security analysis report…
-

How to Write a Cyber Security Report: Essential Tips and Best Practices
As a cyber security professional, it is critical to communicate your findings in a clear and concise manner. A well-written report not only helps you convey the risks and threats to stakeholders but also keeps them informed about mitigation plans and post-incident measures. So, if you have been tasked with writing a cyber security report…
-

Cyber Security Risk Assessment Report Template
Are you looking for a comprehensive cyber security risk assessment report template? Look no further. In this article, we will delve into the world of cyber security risk assessment, providing you with the knowledge and tools necessary to effectively evaluate and mitigate potential risks. As cyber attacks continue to escalate, it is essential for organizations…
-

Cyber Security Incident Report Example
Are you looking for a comprehensive guide to understanding cyber security incident reports? Look no further. In this article, we’ll cover everything you need to know about incident reports from start to finish, including a real-world example. Whether you’re an IT professional, a business owner, or just someone interested in cyber security, this article is…
-

Cyber Security Board Report Template: Your Ultimate Guide
Are you struggling to create a comprehensive and effective cyber security board report? Look no further! In this article, we will provide you with a definitive guide on how to create an excellent cyber security board report template. Whether you are a CEO or a board member, this guide will equip you with the knowledge…
-

How to Prepare a Comprehensive Cyber Security Audit Report Example
Are you concerned about the security of your organization’s data and want to conduct a cyber security audit? Look no further! In this article, we will guide you through the process of creating a comprehensive cyber security audit report example to ensure your organization is well-protected against cyber attacks. Introduction: The internet has become an…
-

Cyber Security After Action Report – Insightful Steps to Improve Your Security Posture
Are you prepared for a cyber attack? It’s not just a matter of if, but when it will happen. Having a strong cyber security posture is critical for modern businesses, and an after action report can help you improve that posture. In this article, we’ll dive into the details of a cyber security after action…
-

Is Zoom Secure for Healthcare? Here’s What You Need to Know
As the world continues to fight against the COVID-19 pandemic, remote communication tools have become essential for various industries. Among them, Zoom has seen a surge in usage, especially in the healthcare sector. But with such sensitive information being shared through these virtual meetings, the question arises, is Zoom secure for healthcare? Is Zoom Secure…
-
How Often Should Healthcare Security Departments Conduct A Security Assessment
Are healthcare organizations conducting security assessments frequently enough to keep pace with ever-evolving cyber threats? Find out the best practices for cybersecurity in healthcare. As the healthcare industry continues to rely more and more on technology, cybersecurity has become a critical issue. Unfortunately, healthcare organizations are increasingly becoming targets of sophisticated cyber attacks. This makes…
-

Healthcare Security Definition: Protecting Vital Information
Are you concerned about the security of your healthcare data? With the increasing number of cyber attacks, it’s essential to understand healthcare security definition. In this article, we’ll dive into what healthcare security means and why it’s crucial to protect vital information. Healthcare security refers to the technologies and protocols used to safeguard sensitive data…
-
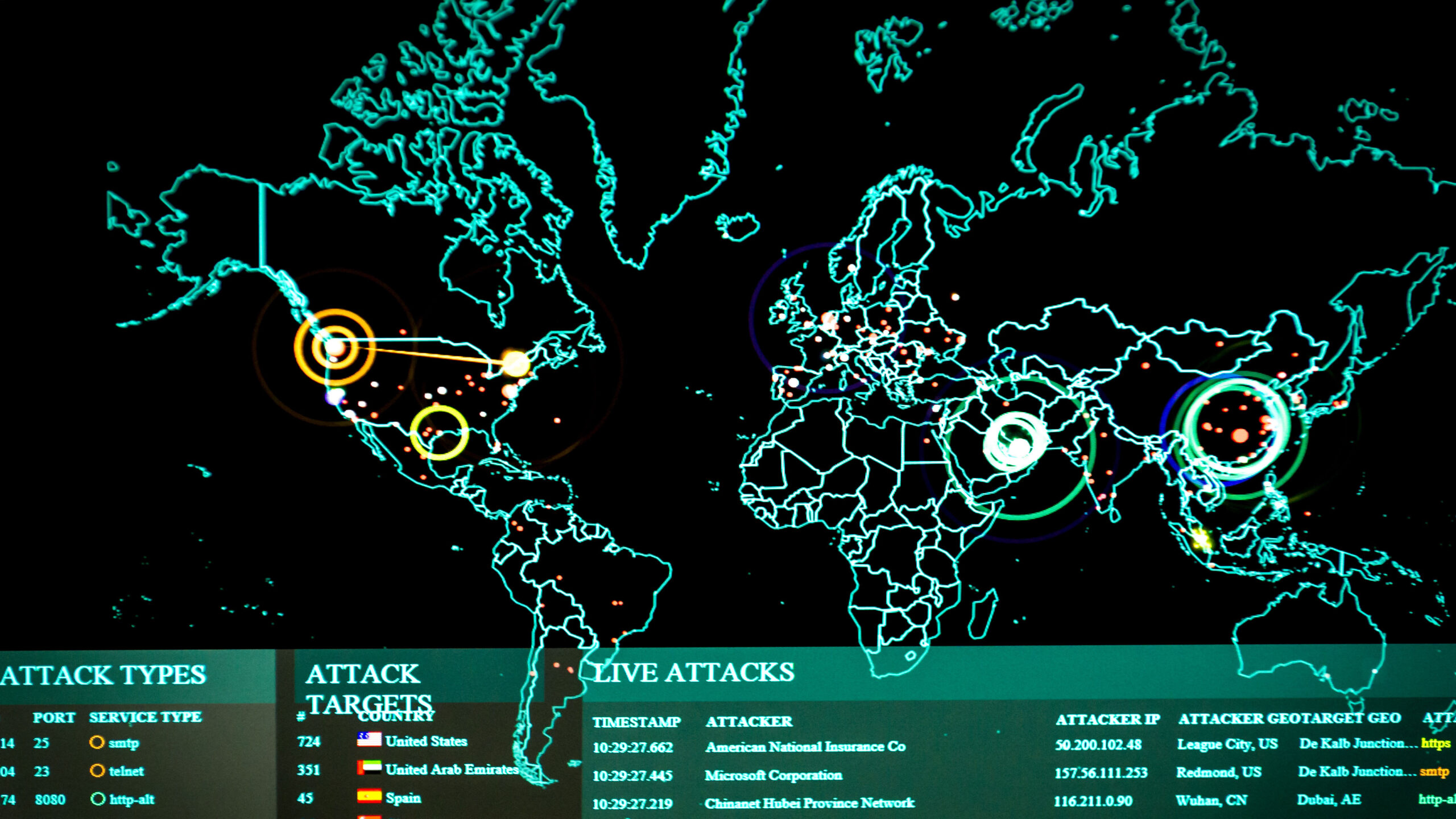
Cyber Attacks And Security Breaches In Healthcare
As cyber attacks become increasingly sophisticated, companies across all industries are at risk of security breaches. However, the healthcare industry has been one of the most targeted sectors for cyber criminals. With the vast amount of sensitive patient information stored online, it is crucial for healthcare organizations to prioritize cybersecurity measures. In this article, we…
-

The Importance of Security in Healthcare: Why it Should be a Top Priority
As we advance further into the digital age, healthcare providers are now utilizing technology at an unprecedented level. While this has brought about numerous benefits for both patients and practitioners alike, it has also brought about new challenges and concerns in terms of cybersecurity. In this article, we will explore why security is paramount in…
-
Why Is Information Security Important In Healthcare
Title: The Vital Role of Information Security in Healthcare First Paragraph: How important is information security in healthcare? The answer is simple – it’s critical. The healthcare industry as a whole is a goldmine for cybercriminals, with sensitive patient information being the prime target. As such, it’s crucial for healthcare organizations to take proactive measures…
-

Information Security in Healthcare: Everything You Need to Know
As cyber threats continue to rise, information security has become an essential component of any industry, particularly healthcare. In this article, we’ll explore what information security entails in healthcare and why it’s crucial to protect sensitive patient data. Healthcare organizations handle vast amounts of personal health information that must be kept confidential. This information includes…
-

Security Design Guidelines For Healthcare Facilities
As cyber threats continue to rise, healthcare facilities are becoming a prime target for malicious attacks. With sensitive data at risk, it’s crucial that security measures are put in place to protect patients’ sensitive information. In this article, we’ll explore the key security design guidelines that every healthcare facility needs to implement to ensure their…
-

Secure Messaging Apps For Healthcare
As the healthcare industry becomes increasingly reliant on digital communication, secure messaging apps have emerged as a crucial tool for protecting sensitive patient data. In this comprehensive guide, we’ll explore the best secure messaging apps for healthcare and how they can help providers stay compliant with HIPAA regulations. Secure Messaging Apps for Healthcare: Why They’re…
-
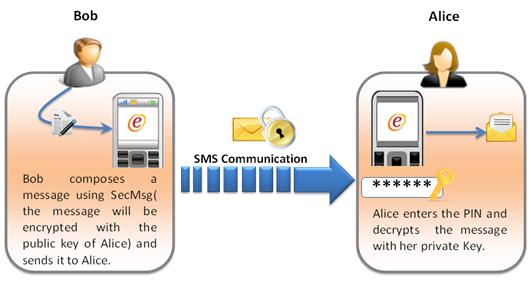
Secure Healthcare Communication: Why it Matters and How to Achieve it
As technology continues to advance, so does the need for secure healthcare communication. In a world where sensitive medical information is constantly being shared, it’s more important than ever to ensure that information is protected from unauthorized access or disclosure. One of the primary concerns with transmitting healthcare information is that it often contains personally…
-
Secure Email for Healthcare: Protecting Sensitive Data
As the healthcare industry evolves, the need for secure communication between healthcare providers and patients is crucial. With electronic communication becoming more prevalent in healthcare, it is important to ensure that sensitive patient data is protected. In this article, we will explore the best practices for secure email in healthcare. Why is secure email crucial…
-

Mobile Device Security In Healthcare
As the use of mobile devices continues to grow in healthcare, the protection of sensitive patient data has become a critical concern. In this article, we’ll explore the importance of mobile device security in healthcare and provide tips on how healthcare organizations can protect their patients’ data. The Importance of Mobile Device Security in Healthcare…
-
Iot Security In Healthcare
As the healthcare industry becomes increasingly reliant on technology, the Internet of Things (IoT) has taken center stage. However, with this increased connectivity comes new security challenges. In this article, we’ll explore IoT security in healthcare and provide insights on how to protect both patients and data. The Importance of IoT Security in Healthcare Healthcare…
Got any book recommendations?